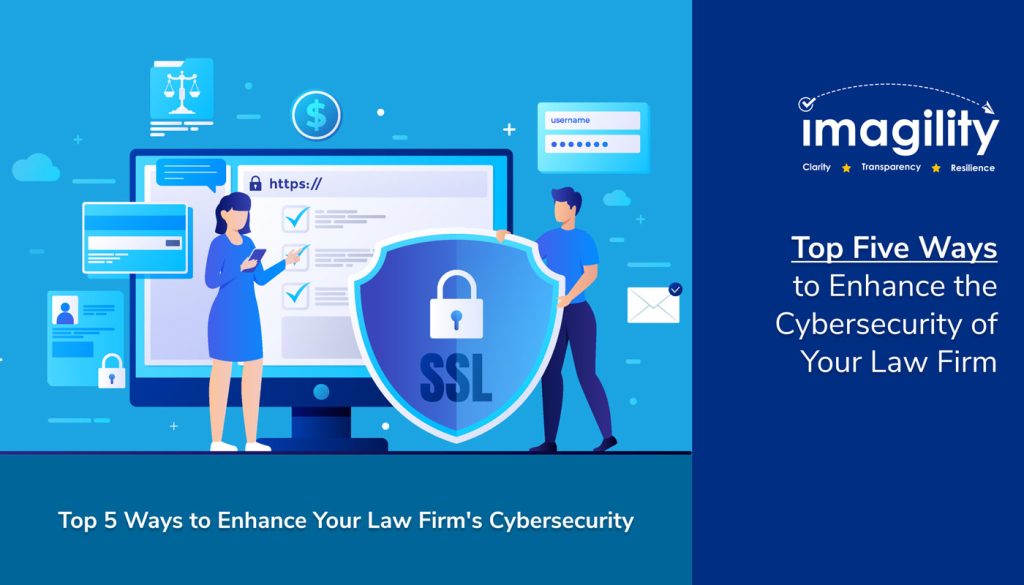
Five Essential Steps to Enhance Your Law Firm’s Cybersecurity
Law firms handle sensitive data and this is one reason why they are increasingly becoming prime targets for cyberattacks. It is crucial to protect the confidentiality of client information, particularly in immigration law. A data breach can compromise your clients’ trust and damage your firm’s reputation, as well. Here are five crucial steps to bolster your law firm’s cybersecurity and how Imagility can be a key partner in this process.
1. Assess and Manage Risks Regularly
The first step is to assess your firm’s current cybersecurity practices. This will help identify any potential vulnerabilities. The assessment could involve conducting internal audits or hiring an external expert to evaluate your systems. Such regular risk assessments will help you stay ahead of potential threats and ensure compliance with cybersecurity regulations.
2. Strengthen Passwords and Secure Your Network
Make sure your passwords are strong and Wi-Fi networks are secure, as they are your first line of defense against cyber threats. Encourage your fellow team members to use complex, unique passwords. Implementing multi-factor authentication wherever possible is also a great way to secure your network. You could further reduce the risk of unauthorized access by securing your network with encryption and creating separate guest networks.
3. Keep Software and Firewalls Up to Date
In most cases, cybercriminals look for vulnerabilities in outdated software they can exploit. Make it a practice to regularly update your software and firewalls to ensure that your systems are protected with the latest security patches. This simple step can significantly reduce the risk of a breach.
4. Utilize Encryption and Data Management Tools
Encryption is crucial for keeping client information safe. Make sure all data is encrypted, whether it’s stored or being sent. Also, control who can access this data by using role-based controls to decide who can view or edit specific information.
5. Evaluate Third-Party Vendors and Establish Cybersecurity Policies
As your firm grows, you can consider evaluating the cybersecurity practices of any third-party vendors you work with. Ensure they have strong security measures in place to protect your data. Additionally, establish clear policies for data retention and disposal to minimize the risk of a breach.
Why Choose Imagility?
Imagility not only simplifies the immigration process but also offers robust cybersecurity features designed to protect your firm’s sensitive data. Imagility is committed to helping you maintain the highest level of security.
Imagility incorporates advanced encryption methods, ensuring that only authorized personnel can access sensitive information. The platform’s network security features help safeguard your data from both internal and external threats. Likewise, Imagility automatically updates its software to include the latest security patches. The platform’s robust firewall management features continuously monitor traffic, providing an additional layer of protection for your data.
Imagility uses industry-leading encryption to protect your data at all times. The platform’s role-based access controls allow you to easily manage who has access to specific information, enhancing the security of your firm. Imagility’s platform offers secure, encrypted cloud storage and file-sharing capabilities. All documents uploaded to the platform are protected by high-level encryption and can be securely shared with clients or colleagues through permission-based access.
Want to see how Imagility can protect your law firm? Schedule a demo today or call us at +1 603 782 4622/+1 617 865 6588 and discover how our platform can keep your data secure while streamlining your work processes.